On-premise & Cloud Protection
Cybersecurity protection is important in every organization
One single security breach can lead to exposing the personal information of millions of people. These breaches have a strong financial impact on the companies and also loss of the trust of customers. Hence, cyber security is very essential to protect businesses and individuals from spammers and cyber criminals. Cyber-criminals can steal your information from government organizations, banks, mobile operators, inernet/telecom companies, health organizations, immigration office…..etc

Voxility runs a powerful global network
On which it can deliver almost any kind of Cloud service, using 22 best-connected data centres in the US and Europe. As a presence list of available services in all 22 data centres around the world.
We are able to increase security performances of your network at a global level and through several high-capacity agreements. We consider your network security as the first choice to build infrastructure solutions and tailored support based on our massive bandwidth capacity, competitive pricing, sprawling product portfolio and network features.


Network security solutions are designed to identify and block these attacks. These solutions include data and access controls such as Data Loss Prevention (DLP), IAM (Identity Access Management), NAC (Network Access Control), and NGFW (Next-Generation Firewall) application controls to enforce safe web use policies.
Advanced and multi-layered network threat prevention technologies include IPS (Intrusion Prevention System), NGAV (Next-Gen Antivirus), Sandboxing, and CDR (Content Disarm and Reconstruction). Also important are network analytics, threat hunting, and automated SOAR (Security Orchestration and Response) technologies.

Mobile devices such as tablets and smartphones have access to corporate data, exposing businesses to threats from malicious apps, zero-day, phishing, and IM (Instant Messaging) attacks. Mobile security prevents these attacks and secures the operating systems and devices from rooting and jailbreaking. When included with an MDM (Mobile Device Management) solution, this enables enterprises to ensure only compliant mobile devices have access to corporate assets.

Web applications, like anything else directly connected to the Internet, are targets for threat actors. Since 2007, OWASP has tracked the top 10 threats to critical web application security flaws such as injection, broken authentication, misconfiguration, and cross-site scripting to name a few.
With application security, the OWASP Top 10 attacks can be stopped. Application security also prevents bot attacks and stops any malicious interaction with applications and APIs. With continuous learning, apps will remain protected even as DevOps releases new content.

As organizations increasingly adopt cloud computing, securing the cloud becomes a major priority. A cloud security strategy includes cyber security solutions, controls, policies, and services that help to protect an organization’s entire cloud deployment (applications, data, infrastructure, etc.) against attack.
While many cloud providers offer security solutions, these are often inadequate to the task of achieving enterprise-grade security in the cloud. Supplementary third-party solutions are necessary to protect against data breaches and targeted attacks in cloud environments.
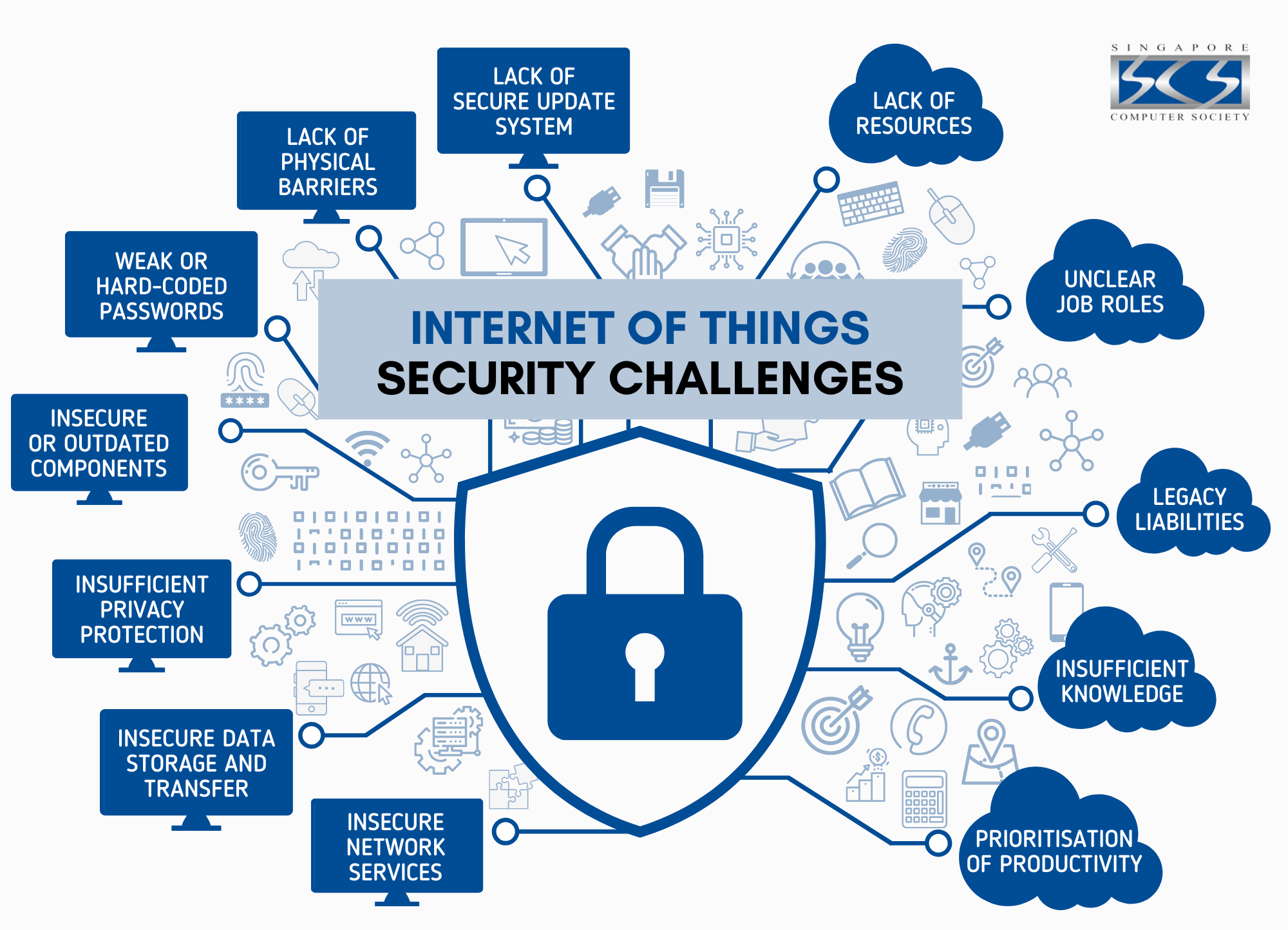
While using Internet of Things (IoT) devices certainly delivers productivity benefits, it also exposes organizations to new cyber threats. Threat actors seek out vulnerable devices inadvertently connected to the Internet for nefarious uses such as a pathway into a corporate network or for another bot in a global bot network.
IoT security protects these devices with discovery and classification of the connected devices, auto-segmentation to control network activities, and using IPS as a virtual patch to prevent exploits against vulnerable IoT devices. In some cases, the firmware of the device can also be augmented with small agents to prevent exploits and runtime attacks.

Endpoint Security
The zero-trust security model prescribes creating micro-segments around data wherever it may be. One way to do that with a mobile workforce is using endpoint security. With endpoint security, companies can secure end-user devices such as desktops and laptops with data and network security controls, advanced threat prevention such as anti-phishing and anti-ransomware, and technologies that provide forensics such as endpoint detection and response (EDR) solutions.
Our company can provide high Accuracy in detection at different network security solutions such as;
Network cloud security
On-premises network security
Application security
Identity Management and Data Security
Mobile Security
Disaster Recovery and Business Continuity Planning
Unlimited attack support
5Tbps bandwidth
Unlimited clean traffic
Unlimited protection for levels 3, 6, 7
Always on protection
Online update and notifications
Online support
Online customer dashboard and control
Smart detecting that the UDP legitimate traffic
We have the capacity to offer the lowest competitive prices and 100% secure your network. Our company is capable to offer 100Mb-500GB clean traffic bandwidth.
CYBERSECURITY is “CONFIDENTIALITY, INTEGRITY, AVAILIBILITY”

